I am attempting to implement claims based authentication to the back office (7.4.3) with an on-premise AD FS server using WS-Federation.
I have followed the steps in identity provider documentation and the provider button is showing as expected at the login screen.
However, after a succesful login at the federation server I receive this error "The requested provider (https://logon.domain.tld/adfs/services/trust) has not been linked to to an account", even though I added ExternalSignInAutoLinkOptions.
When logging in to the back office with an existing user the button for manual account linking is shown. Unfortunately, nothing appears to happens when it is clicked:
My Owin startup and authentication extensions look like this:
public class ConfigureOwinStartup
{
public static void Configuration(IAppBuilder app)
{
// Configure back office users membership provider
app.ConfigureUserManagerForUmbracoBackOffice(
ApplicationContext.Current,
MembershipProviderExtensions.GetUsersMembershipProvider().AsUmbracoMembershipProvider());
// Ensure OWIN is configured for Umbraco back office authentication
app.UseUmbracoBackOfficeCookieAuthentication(ApplicationContext.Current)
.UseUmbracoBackOfficeExternalCookieAuthentication(ApplicationContext.Current);
app.UseCookieAuthentication(new CookieAuthenticationOptions
{
AuthenticationType = DefaultAuthenticationTypes.ApplicationCookie
});
// Configure additional back office authentication options
app.ConfigureBackOfficeAdfsAuthentication();
}
}
public static class AdfsAuthenticationExtensions
{
public static void ConfigureBackOfficeAdfsAuthentication(
this IAppBuilder app,
string caption = "AD FS",
string style = "btn-microsoft",
string icon = "fa-windows")
{
var adfsMetadataEndpoint = ConfigurationManager.AppSettings["AdfsMetadataEndpoint"];
var adfsRelyingParty = ConfigurationManager.AppSettings["AdfsRelyingParty"];
var wsFedOptions = new WsFederationAuthenticationOptions
{
Wtrealm = adfsRelyingParty,
MetadataAddress = adfsMetadataEndpoint,
AuthenticationType = WsFederationAuthenticationDefaults.AuthenticationType,
SignInAsAuthenticationType = Constants.Security.BackOfficeExternalAuthenticationType,
Caption = caption
};
wsFedOptions.SetExternalSignInAutoLinkOptions(new ExternalSignInAutoLinkOptions(autoLinkExternalAccount: true));
wsFedOptions.ForUmbracoBackOffice(style, icon);
app.UseWsFederationAuthentication(wsFedOptions);
app.SetDefaultSignInAsAuthenticationType(WsFederationAuthenticationDefaults.AuthenticationType);
}
}
My relying party is configured with this claims rule at the AD FS server:
When I was looking how to integrate ADFS with Umbraco I have the same issue. Something useful was to debug the umbraco source code and see how the authentication workflows run.
Try explicitly setup the property wsFedOptions.AuthenticationType after the invocation of: wsFedOptions.ForUmbracoBackOffice(style, icon);.
In my case that was the key to get this working. The value for this property must be the URI: https://logon.domain.tlf/adfs/services/trust
Active Directory makes the authentication type 'special'. It's probably different depending on the type of AD you are using as well. The AuthenticationType parameter is how the linking of accounts works, and relies on that value being returned from the OAuth provider. This is also the value stored in the umbracoExternalLogin table.
You can also see in this snippet that ForUmbracoBackOffice is called before the AuthenticationType is set, since as you previously noted, ForUmbracoBackOffice will change the auth type provided to be prefixed - since this is needed for most oauth providers.
The code base appears to be oauth centric when looking at naming conventions in both frontend and backend. I don't know if an override with a more generic approach could/should be implemented or you will OAuth everything?
Great write up Sam, thanks! Been meaning to update my guide for ages to include groups. This should really be included in the docs. There is an open ticket with my name on it currently. :)
Account (auto)linking not working with Owin AD FS/WS-Federation authentication
I am attempting to implement claims based authentication to the back office (7.4.3) with an on-premise AD FS server using WS-Federation.
I have followed the steps in identity provider documentation and the provider button is showing as expected at the login screen.
However, after a succesful login at the federation server I receive this error "The requested provider (https://logon.domain.tld/adfs/services/trust) has not been linked to to an account", even though I added ExternalSignInAutoLinkOptions.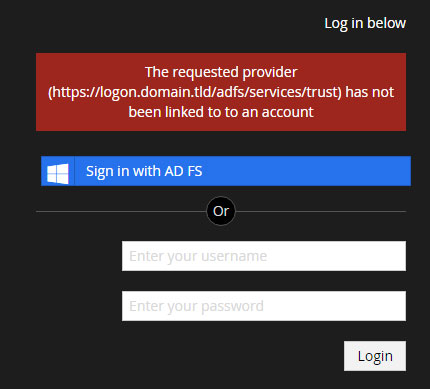
When logging in to the back office with an existing user the button for manual account linking is shown. Unfortunately, nothing appears to happens when it is clicked:
My Owin startup and authentication extensions look like this:
My relying party is configured with this claims rule at the AD FS server: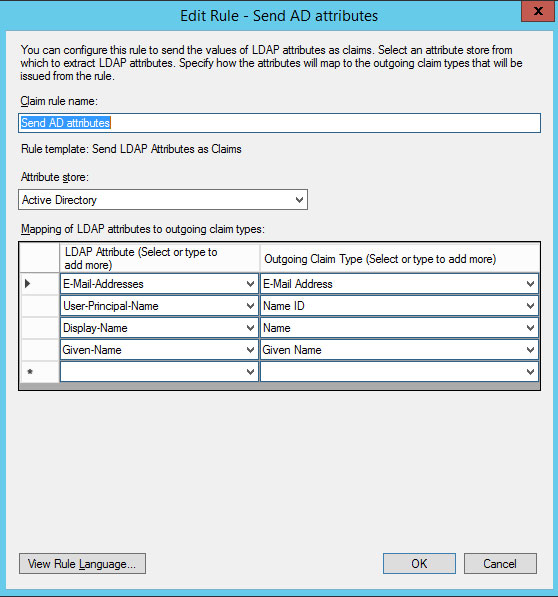
Hi Frederik,
When I was looking how to integrate ADFS with Umbraco I have the same issue. Something useful was to debug the umbraco source code and see how the authentication workflows run.
Try explicitly setup the property
wsFedOptions.AuthenticationTypeafter the invocation of:wsFedOptions.ForUmbracoBackOffice(style, icon);. In my case that was the key to get this working. The value for this property must be the URI:https://logon.domain.tlf/adfs/services/trustFull example working (for u7.3.8) https://gist.github.com/eerrecart/4760b245ac78d5915b55ac311de39065
Another thing to check is that you are providing all the fields (claims) that umbraco needs, this can be done seeing the source code of:
https://github.com/umbraco/Umbraco-CMS/blob/75c2b07ad3a093b5b65b6ebd45697687c062f62a/src/Umbraco.Web/Security/Identity/AuthenticationManagerExtensions.cs
Method:
GetExternalLoginInfoalso a good point to start debuging the external login flow.Elias
Hi Elias
Thank you very much. It was the wsFedOptions.ForUmbracoBackOffice() overwriting my AuthenticationType property.
Now I only have to figure out why the backend linking button does not trigger any action. :)
Kind regards
Frederik
Active Directory makes the authentication type 'special'. It's probably different depending on the type of AD you are using as well. The AuthenticationType parameter is how the linking of accounts works, and relies on that value being returned from the OAuth provider. This is also the value stored in the
umbracoExternalLogintable.The only real example I can give you is the snippet we use in Identity Extensions when configuring Azure AD OAuth, you can see that here: https://github.com/umbraco/UmbracoIdentityExtensions/blob/master/src/App_Start/UmbracoADAuthExtensions.cs#L65
You can also see in this snippet that
ForUmbracoBackOfficeis called before the AuthenticationType is set, since as you previously noted,ForUmbracoBackOfficewill change the auth type provided to be prefixed - since this is needed for most oauth providers.Hi Shannon
Thanks for your feedback. I got it working in the end. I just created a bug report here, before seing your answer: http://issues.umbraco.org/issue/U4-8848
The code base appears to be oauth centric when looking at naming conventions in both frontend and backend. I don't know if an override with a more generic approach could/should be implemented or you will OAuth everything?
Hi Frederik, could you provide your final code in a full working example. Until now I had no luck with my implementations.
Hi Klaus
You can find a a link to a full test site in my 24 Days post here: http://24days.in/umbraco-cms/2016/authenticating-with-ad-fs-and-identityextensions/
Account linking works fine but I have experienced some issues with different token life times in Umbraco and the ad fs server.
/Frederik
Hi Klaus
You can find a a link to a full test site in my 24 Days post here: http://24days.in/umbraco-cms/2016/authenticating-with-ad-fs-and-identityextensions/
Account linking works fine but I have experienced some issues with different token life times in Umbraco and the ad fs server.
/Frederik
Hi
i'm getting the same error The requested provider (http://myadfsdomain.com/adfs/services/trust) has not been linked to to an account
I've tried to setup the property
wsFedOptions.AuthenticationTypeafter the invocation of:wsFedOptions.ForUmbracoBackOffice(style, icon);But no luck.i'm getting the below claims from the adfs server
My code is
i also tried with the sample project available in http://24days.in/umbraco-cms/2016/authenticating-with-ad-fs-and-identityextensions/ . But Same error i am getting.
I've tried in Umbraco versions 7.7.4 and 7.7.6
Thanks, Sriram
Hi @sriram I have the same problem. Did you figure this out?
/ br Lars
Hello Sriam
I am afraid haven't tested this solution in recent builds. If you have a hybrid setup Azure AD might be an option instead? /Frederik
I've written some instructions on how to use the auto link and how to sync AD groups to Umbraco groups: https://medium.com/@samuel.sperling/authenticating-with-ad-fs-in-umbraco-12d1a4c6777e
Great write up Sam, thanks! Been meaning to update my guide for ages to include groups. This should really be included in the docs. There is an open ticket with my name on it currently. :)
is working on a reply...